Nowadays, as you know, nothing is private and secure in the digital world. These days online privacy and security are a difficult challenge to handle, and it has become a toy that hackers love to play with. Then, web trackers and business profiles track our browsing activities to push ads. Cybersecurity professionals recommend Virtual Private Network apps, anonymous browsers, web trackers, and ad-blockers to avoid such issues.
One such tool, like VPN, creates an encrypted tunnel between your device and the internet, providing an additional security layer. A VPN can protect your data from eavesdropping and provide anonymity by masking your IP address. Seems like anonymous browsers like Tor browser are designed to enhance privacy and security by routing your internet traffic, which makes it difficult to trace your online activities.
These VPNs can provide additional protection, but no system is foolproof. Threats and vulnerabilities are constantly evolving, and maintaining good security practices, such as regularly updating your software, using strong passwords, and being cautious with online interactions, is essential. In this blog, we provide you deep web links/URLs with its features to give you the best alternative Tor browser to run smoothly.
Do Tor Networks Provide Access to Deep Web Links?
Yes, the Tor network is commonly used for accessing websites on the deep web. The Tor network, also known as the Darknet or Dark Web, is an overlay network that provides anonymous communication. It allows users to access websites and services that are not indexed by traditional search engines and are typically not accessible through regular web browsers.
The Tor network achieves anonymity by encrypting and routing internet traffic through a series of relays, making it difficult to trace the origin and destination of the data. This anonymity makes it a popular choice for individuals who wish to access websites on the deep web, which includes various types of content, ranging from legitimate uses like privacy-oriented forums to illicit activities like black markets.
List of 12 Best Tor Browser Alternatives
While the Tor Browser is one of the most popular and widely used tools for accessing the Tor network, there are a few alternative browsers and privacy-focused tools that you may consider. Here are some notable Tor Browser alternatives:
1. I2P
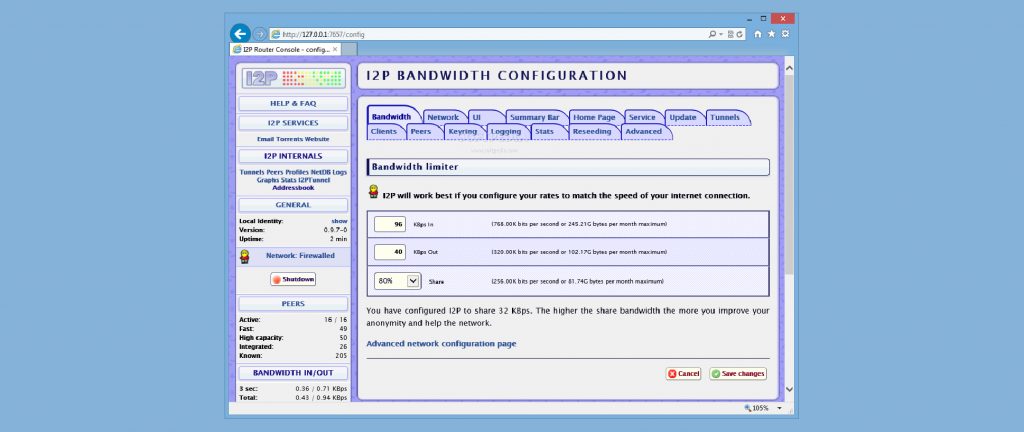
This is the official I2P browser, and it is available for Windows, macOS, and Linux. It is a simple and easy-to-use browser that provides a number of features that make it easier to browse I2P sites, such as a built-in search engine and a list of known I2P sites.
I2P allows secure and private communication over the Internet. It is designed to protect user privacy and resist censorship by routing traffic through a decentralized network of volunteer-run nodes. While I can provide information about I2P, I cannot verify or provide official statements about specific software products.
With I2P, you can make internet traffic untraceable on the internet by sending it through thousands of distributed computers. Moreover, the only drawbacks are I2P provides a slow browsing session because its algorithm and system are similar to the Tor network.
2. Epic Browser
Epic Browser is a web browser that aims to provide users with enhanced privacy and security features while browsing the internet. It is based on the Chromium open-source project, which forms the foundation for popular browsers like Google Chrome.
One of the key features of Epic Browser is its focus on privacy. It incorporates several tools and settings to minimize user tracking and data collection. For example, it blocks third-party cookies by default, which helps prevent advertisers and websites from tracking users across different sites. Epic Browser also has a built-in encrypted proxy known as Epic Proxy, which encrypts and routes users’ internet traffic through a proxy server, providing an additional layer of privacy.
To protect against online tracking, Epic Browser offers a feature called “Epic Privacy Browser Blocks.” This feature blocks various types of tracking scripts, including social media widgets, advertising networks, and analytics trackers, aiming to reduce the amount of data collected about the user.
Epic Browser is available for Windows and macOS operating systems and is generally free to use. It is important to note that while Epic Browser emphasizes privacy and security, no browser can guarantee complete anonymity or protection from all online threats. Users should still exercise caution, keep their software up to date, and follow good security practices while browsing the internet.
3. FreeNet
Freenet is a peer-to-peer platform that facilitates censorship-resistant communication and publishing. It operates on a decentralized network to promote freedom of speech and preserve user privacy. Freenet uses a distributed data store, where participating nodes store and serve content to other nodes in the network.
Freenet supports two main modes of operation: OpenNet and Darknet. In OpenNet mode, Freenet nodes connect to random nodes in the network, sharing information across a broad range of users. This mode emphasizes openness and encourages sharing content with a wider audience.
On the other hand, Darknet mode enables users to form private, invitation-only networks within Freenet. Darknet communities typically have their own specific interests or themes, and users must know someone within the network to join. Darknet mode provides increased privacy and security, limiting access to content to trusted individuals within the network.
Freenet uses strong encryption to ensure the confidentiality and integrity of data transmitted within the network. It employs various techniques such as data splitting, redundant storage, and caching to provide resilience against censorship attempts and ensure content availability.
4. Comodo IceDragon
Comodo IceDragon is a web browser developed by Comodo Group, a cybersecurity company known for its suite of security products. IceDragon is based on the Mozilla Firefox open-source project and aims to provide users with enhanced privacy and security features while browsing the internet.
One of the notable features of Comodo IceDragon is its emphasis on security. It incorporates Comodo’s expertise in cybersecurity to deliver a browser that helps protect users from various online threats. IceDragon includes Comodo’s SiteInspector technology, which scans websites for potential malware and phishing attempts, providing a warning if a site is flagged as suspicious or dangerous.
In terms of privacy, IceDragon offers several features to enhance user confidentiality. It includes a privacy-focused mode called “Private Browsing,” allowing users to browse the web without storing browsing history, cookies, or other temporary data. Additionally, IceDragon blocks third-party cookies by default, reducing the ability of advertisers and websites to track user activity across different sites.
5. Yandex Browser
Yandex Browser is a web browser developed by Yandex, a Russian technology company known for its search engine and other online services. Yandex Browser is based on the Chromium open-source project, which forms the foundation for popular browsers like Google Chrome.
Yandex Browser offers a range of features designed to provide a fast and personalized browsing experience. One of its notable features is Turbo Mode, which aims to optimize browsing speed by compressing web pages and reducing data usage. Particularly useful in areas with slow internet connections.
Yandex takes privacy and security seriously and incorporates various measures to protect user data. Yandex Browser includes built-in protection against malware and phishing attempts, warning users if they navigate to potentially harmful websites. It also utilizes secure protocols for encrypted connections, helping to safeguard sensitive information during online transactions.
In terms of the user interface, Yandex Browser offers a clean and user-friendly design, with a customizable new tab page that displays frequently visited sites, bookmarks, and a Yandex search bar. It also includes a built-in translator, enabling users to translate web pages into different languages.
6. Tails
Tails Browser is a modified version of the Tor Browser that is included in the Tails operating system. This browser has a security-focused operating system designed to protect your privacy and anonymity. The Tails Browser is configured with a number of security features, such as:
Tor: The Tails Browser uses the Tor network to anonymize your traffic. Tor is a free and open-source software that allows you to route your internet traffic through a series of volunteer-operated servers, making it difficult for anyone to track your online activity.
HTTPS Everywhere: The Tails Browser includes the HTTPS Everywhere extension, which automatically encrypts your traffic whenever possible. This helps protect your privacy and security when browsing the web.
NoScript: The Tails Browser also includes the NoScript extension, which blocks all JavaScript by default. JavaScript is a programming language that is often used to track users and inject ads into websites. By blocking JavaScript, you can help to protect your privacy and security.
In addition to these security features, the Tails Browser also includes several other features designed to make it easier to use the Tor network. These features include a Built-in Tor configuration, an easy-to-use interface, and a portable operating system that can help you to protect your privacy.
7. Subgraph OS
Subgraph OS is a security-focused operating system designed to provide enhanced privacy and protection for users. It is based on the Linux operating system and incorporates various security features and technologies to create a hardened and secure environment.
The primary goal of Subgraph OS is to protect users against targeted attacks, surveillance, and exploitation attempts. It achieves this through several key security measures:
Application Sandboxing: Subgraph OS employs strict application sandboxing techniques to isolate programs and restrict their access to sensitive system resources. This helps mitigate the impact of potential vulnerabilities or malicious code by containing them within their own sandboxed environments.
System Hardening: The operating system is hardened with a focus on minimizing attack vectors and reducing the potential for exploitation. This includes proactive security measures such as address space layout randomization (ASLR), stack smashing protection (SSP), and strict memory protections.
Enhanced Network Security: Subgraph OS incorporates network-level protections to defend against various network-based attacks. It includes a built-in firewall that blocks unwanted incoming and outgoing connections and employs network address translation (NAT) to help conceal the user’s IP address.
Tor Integration: Subgraph OS integrates with the Tor network, allowing users to route their internet traffic through the Tor network for enhanced privacy and anonymity. This helps protect against traffic analysis and censorship attempts.
Application Security Auditing: Subgraph OS includes an application auditing system called Oz, which monitors and restricts the behavior of applications to prevent potentially malicious actions. It can limit file system access, restrict network connections, and monitor inter-process communication, providing an additional layer of security.
8. Waterfox
Waterfox is an open-source web browser that is based on Mozilla Firefox. It was developed with the goal of providing users with a fast, secure, and privacy-focused browsing experience. Waterfox was created by Alex Kontos, a software developer from Scotland, who was motivated to build a browser that addressed some of the users’ concerns with mainstream browsers.
One of the main features of Waterfox is its focus on privacy. It strives to minimize data collection and tracking, giving users more control over their online activities. By default, Waterfox blocks trackers disables telemetry, and avoids connecting to certain websites that are known to compromise user privacy. Additionally, it supports various privacy-focused extensions that users can install to enhance their browsing privacy further.
Waterfox also emphasizes performance and speed. It is built on Mozilla’s Firefox codebase but is optimized for 64-bit systems, making use of the full potential of modern hardware. This optimization results in improved performance and faster page loading times, particularly for users with more powerful computers.
9. SRWare Iron
SRWare Iron is a web browser that aims to provide users with a secure, privacy-focused browsing experience. It is based on the Chromium open-source project, which also serves as the foundation for Google Chrome. However, SRWare Iron distinguishes itself by addressing certain privacy concerns associated with Chrome and implementing additional security measures.
The primary focus of SRWare Iron is user privacy. It takes a proactive approach to safeguarding personal information by disabling or removing various components that may collect user data. For instance, Iron eliminates features such as Google’s usage tracking, URL suggestions, and error reporting. Doing so aims to reduce the amount of data shared with third parties and enhance user anonymity while browsing the web.
One of the key privacy-oriented features of SRWare Iron is the omission of the unique user ID, commonly known as the “client ID” or “user ID,” which is employed by Chrome for identification and tracking purposes. By removing this identifier, Iron aims to prevent the correlation of browsing activities across multiple websites and enhance user privacy.
Furthermore, SRWare Iron integrates additional security measures to protect users from potential threats. It includes built-in ad-blocking capabilities that help eliminate intrusive advertisements and prevent malicious scripts from executing. This feature enhances browsing speed and reduces the risk of encountering harmful content.
10. Brave
Brave is a popular web browser for its privacy-centric approach, speed, and unique features. Created by Brendan Eich, the co-founder of Mozilla Firefox and creator of JavaScript, Brave aims to provide users with a fast and secure browsing experience while addressing the issue of online privacy.
One of the key features of Brave is its strong emphasis on user privacy. By default, Brave blocks website trackers, intrusive ads, and other elements that can compromise user privacy and slow down browsing speed. It also incorporates HTTPS Everywhere, automatically upgrading connections to the more secure HTTPS protocol when available. These privacy-focused measures help protect users from tracking, profiling, and potential security vulnerabilities.
Brave also introduces an innovative system called Brave Shields, which provides granular control over website elements such as ads, scripts, and cookies. Users can choose to block or allow specific elements, giving them a high level of customization and control over their browsing experience.
11. Pale Moon

Pale Moon is an open-source web browser that prioritizes speed, customization, and user control. It originated from the Mozilla Firefox codebase but has diverged over time to create its own unique browser experience. The development team behind Pale Moon focuses on maintaining compatibility with existing Firefox add-ons while providing a streamlined and privacy-conscious browsing experience.
One of the key aspects of Pale Moon is its emphasis on speed. The browser is optimized for performance, utilizing a lightweight design and efficient resource management. This allows for faster page loading times and smoother browsing, particularly on older or lower-specification systems.
Pale Moon also offers extensive customization options, allowing users to tailor their browsing experience to their preferences. It provides a range of configuration settings and advanced options that can be adjusted to suit individual needs. Users can modify various browser aspects, such as the user interface and toolbar layout, and even turn specific features on or off to create a personalized browsing environment.
12. Iridium Browser

Iridium Browser is a privacy-focused web browser built on the Chromium open-source project. It aims to provide users with a secure and privacy-enhanced browsing experience by disabling or removing features that could collect user data while still offering compatibility with Chrome extensions.
Privacy is a primary focus of the Iridium Browser. It takes a proactive approach to protect user data by disabling or removing various components that may compromise privacy. For instance, it turns off Google’s usage tracking, URL suggestions, and search suggestions, which can help prevent the collection and sharing of personal information.
By default, Iridium Browser also blocks third-party cookies commonly used for tracking purposes. This further enhances user privacy by preventing advertisers and other entities from monitoring online activities across multiple websites.
In addition to these privacy enhancements, Iridium Browser integrates various security features. It supports secure connections through HTTPS and implements security patches and updates from the Chromium project to protect against potential vulnerabilities.
FAQ’s
The Tor network is not part of the dark web but is often used to access it. The dark web is a part of the internet that is not indexed by search engines and requires special software to access. Tor is one of the most popular ways to access the dark web.
Tor is a free and open-source software that helps you defend against traffic analysis, a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security. Tor directs Internet traffic through a worldwide volunteer overlay network consisting of more than 7,000 relays to conceal a user’s location and usage from anyone conducting network surveillance or traffic analysis.
Not all websites work on Tor. Some websites block Tor traffic because they are concerned about security or do not want to be associated with the Tor network.
Here are some of the reasons why a website might block Tor traffic:
Security: Some websites block Tor traffic because they are concerned about security. Tor is a popular tool for criminals, and some websites do not want to be associated with criminal activity.
Legitimacy: Some websites block Tor traffic because they do not want to be associated with the Tor network. The Tor network has a reputation for being used for illegal activities, and some websites do not want to be seen as condoning these activities.
Performance: Some websites block Tor traffic because it can slow down their servers. Tor traffic is routed through a series of volunteer-operated servers, which can cause performance issues for websites not designed to handle Tor traffic.
Yes, you can go on Tor without a VPN. However, there are some security risks associated with doing so.
When you use Tor without a VPN, your traffic is routed through a series of volunteer-operated servers. This can help to protect your privacy, but it does not completely anonymize your traffic. If someone is monitoring the Tor network, they may be able to see that you are using Tor and track your traffic to the exit node.
No, Tor is not a VPN. Tor is a free and open-source software that helps you defend against traffic analysis, a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security.
Tor directs Internet traffic through a worldwide volunteer overlay network consisting of more than 7,000 relays to conceal a user’s location and usage from anyone conducting network surveillance or traffic analysis.
